本文主要是介绍【TCPDUMP 笔记 2022.8.18】,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
【TCPDUMP 笔记 2022.8.18】
- TCP协议
- tcp(transmission control protocol)传输控制协议
- TCP的6个标志位(Flag)
- TCPDUMP数据包内容解释
- TCPDUMP常见过滤规则参数
- 基于IP地址过滤 参数 host 截获特定主机的收发数据包
- 截获特定方向的数据包 目的地址 dst 源地址 src
- 截获特定网段的数据包 net
- 基于端口的过滤规则 port (src port 、dst port)
- 基于协议过滤 protocal (网络层、传输层协议)
- h 帮助命令
- i 指定网卡, tcp -i any 监听所有网卡
- w
- r
- n
- nn
- N 不打印出host的域名部分,比如域名www.baidu.com,只显示www. 10.0.0.128,只显示10
- t 不输出时间
- tt 输出时间戳
- ttt 输出每两行打印的时间间隔
- tttt
- v
- vv 更详细
- vvv
- c
- 参数C
- Q
- q
- D 显示所有可用的网络接口列表。
- L 列出网络接口的已知数据链路
- s
- V 查看版本
- A 以ASCII格式(真实内容)打印出所有的分组并且读取此文件
- 配合grep使用
- X 表示同时使用十六进制和ASCII字符串打印报文的全部数据, X 和 A两个参数不能同时使用
- e
- -F
- -l
- TCPDUMP过滤规则组合--逻辑运算
- 逻辑运算符:and or not
- **and例子**
- **or例子**
- **not例子**
- TCPDUMP高级过滤
- 基于 包大小进行过:查看指定大小的数据包 less greater
- 补充 ALG穿透 SIP
- 详情描述
TCP协议
tcp(transmission control protocol)传输控制协议
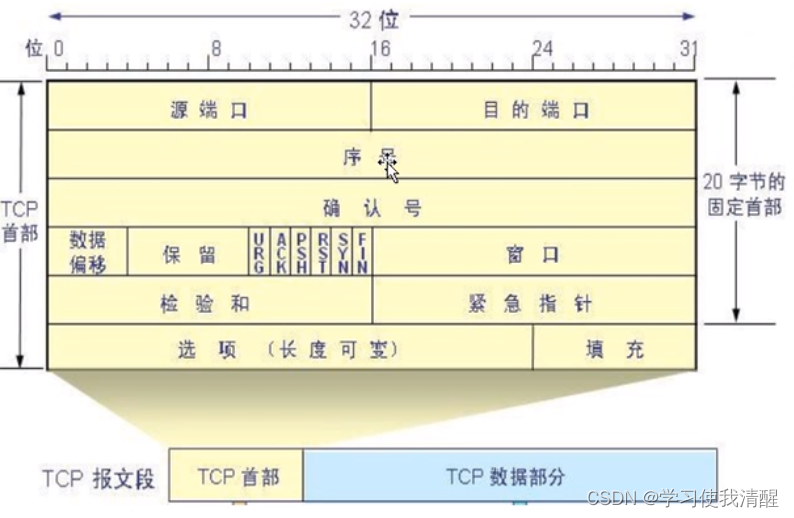
- 1 序号:每个数据包都有对应的一个序列号。(保证可靠性)
- 2 确认号:每发送1个数据包都需要收到对应的确认包,确认号=序号+1
- 3 窗口:滑动窗口,提高可靠性 提高报文发送效率,例如迟迟未收到确认号,会默认为数据包丢失需要重传,如果每个数据包都在等待确认号,会有一些延迟,导致堆积,降低发包效率,滑动窗口用于缓冲,也可发送一部分未收到确认号的数据。
TCP的6个标志位(Flag)
- 三次握手建立连接,四次挥手断开连接)
- 1 SYN:连接请求或者接受连接请求,(DNS协议默认是UDP的53端口)。
- 2 FIN:连接结束,断开连接
- 3 RST:重置连接(reset)
- 4 ACK:确认标记位
- 5 PSH:催促标记位,将接受缓冲区内数据向上交付给应用程序,而不是等待缓冲区满后再交付。
- 6 URG:紧急标志位,将紧急数据排在普通数据的前面。
- 7 .:没有Flag(意思是除了S(开始连接),P(推送数据),F(结束连接),R(重置连接)四种类型外的其他情况,有可能是ACK也有可能是URG)。
TCPDUMP数据包内容解释
- TCPdump是Linux里常用的网络抓包工具(以centos 7.9虚拟机为例, 虚拟机IP10.0.0.128 宿主机IP 10.0.61.61 )
- 输入tcpdump会默认抓取第一个网络接口上所有的数据包,本机的第一个网卡是eth0。
[root@aaa ~]# tcpdump
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
09:21:15.799011 IP bogon.54416 > bogon.ssh: Flags [.], ack 1725626776, win 4101, length 0
09:30:57.017185 IP bogon.ssh > bogon.54416: Flags [P.], seq 35244:35472, ack 53, win 264, length 228
- 第一列:时间
- 第二列:网络协议 IP
- 第三列:发送方的IP地址+端口号,其中bogon是主机号,54416是端口号。
- bogon(名词):虚伪的人,沼泽林,人名(博贡)
- 第四列:箭头表示数据的流向
- 第五列:接收方的IP地址和端口号
- 第六列:数据包内容,包括Flags标识符,seq号,ack号,win窗口,数据长度,其中[P.]表示PUSH标志位协议为1。
TCPDUMP常见过滤规则参数
基于IP地址过滤 参数 host 截获特定主机的收发数据包
如目的主机IP为10.0.61.61
[root@aaa ~]# ping 10.0.61.61
PING 10.0.61.61 (10.0.61.61) 56(84) bytes of data.
64 bytes from 10.0.61.61: icmp_seq=1 ttl=128 time=0.500 ms
64 bytes from 10.0.61.61: icmp_seq=2 ttl=128 time=2.09 ms
64 bytes from 10.0.61.61: icmp_seq=3 ttl=128 time=0.860 ms
- 此时查看tcpdump抓包
[root@aaa ~]# tcpdump host 10.0.61.61
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
11:34:52.801820 IP bogon > bogon: ICMP echo request, id 2767, seq 1, length 64
11:34:52.802349 IP bogon > bogon: ICMP echo reply, id 2767, seq 1, length 64
11:34:53.803277 IP bogon > bogon: ICMP echo request, id 2767, seq 2, length 64
11:34:53.803719 IP bogon > bogon: ICMP echo reply, id 2767, seq 2, length 64
11:34:54.805727 IP bogon > bogon: ICMP echo request, id 2767, seq 3, length 64
11:34:54.806352 IP bogon > bogon: ICMP echo reply, id 2767, seq 3, length 64
6 packets captured
6 packets received by filter
0 packets dropped by kernel
截获特定方向的数据包 目的地址 dst 源地址 src
- src 报文全部是reply响应报文
[root@aaa ~]# tcpdump src 10.0.61.61
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
11:39:13.304872 IP bogon > bogon: ICMP echo reply, id 2770, seq 1, length 64
11:39:14.309917 IP bogon > bogon: ICMP echo reply, id 2770, seq 2, length 64
11:39:15.309531 IP bogon > bogon: ICMP echo reply, id 2770, seq 3, length 64
3 packets captured
3 packets received by filter
0 packets dropped by kernel
- dst 报文全部是request响应报文
[root@aaa ~]# tcpdump dst 10.0.61.61
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
11:39:39.655989 IP bogon > bogon: ICMP echo request, id 2772, seq 1, length 64
11:39:40.656705 IP bogon > bogon: ICMP echo request, id 2772, seq 2, length 64
11:39:41.657465 IP bogon > bogon: ICMP echo request, id 2772, seq 3, length 64
3 packets captured
3 packets received by filter
0 packets dropped by kernel
截获特定网段的数据包 net
- 发起对60网段的ping
[root@aaa ~]# ping 10.0.60.2
PING 10.0.60.2 (10.0.60.2) 56(84) bytes of data.
64 bytes from 10.0.60.2: icmp_seq=1 ttl=128 time=1.43 ms
64 bytes from 10.0.60.2: icmp_seq=2 ttl=128 time=1.08 ms
64 bytes from 10.0.60.2: icmp_seq=3 ttl=128 time=1.37 ms
--- 10.0.60.2 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2007ms
rtt min/avg/max/mdev = 1.081/1.297/1.436/0.160 ms
- tcpdump抓取
[root@aaa ~]# tcpdump net 10.0.60.0/24
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
11:45:17.092016 IP bogon > bogon: ICMP echo request, id 2785, seq 1, length 64
11:45:17.093414 IP bogon > bogon: ICMP echo reply, id 2785, seq 1, length 64
11:45:18.095154 IP bogon > bogon: ICMP echo request, id 2785, seq 2, length 64
11:45:18.096197 IP bogon > bogon: ICMP echo reply, id 2785, seq 2, length 64
11:45:19.099199 IP bogon > bogon: ICMP echo request, id 2785, seq 3, length 64
11:45:19.100524 IP bogon > bogon: ICMP echo reply, id 2785, seq 3, length 64
基于端口的过滤规则 port (src port 、dst port)
- 如或者http协议80端口的数据包
[root@aaa ~]# tcpdump tcp port 80
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
- 截获多个端口数据。
[root@aaa ~]# tcpdump tcp port 80 or (port) 443 # port可有可无
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
- 抓取范围端口
[root@aaa ~]# tcpdump portrange 8000-8080
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
- 常用的协议如http ,https,也可直接加协议名称。
[root@aaa ~]# tcpdump tcp port http
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
基于协议过滤 protocal (网络层、传输层协议)
- 截获ICMP协议的报文,例如ip、ip6、arp、tcp、udp等,
- 注意:https,dns、ssh等应用层协议需要用语法 tcpdump port http
[root@aaa ~]# tcpdump icmp
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
h 帮助命令
[root@aaa ~]# tcpdump -h
tcpdump version 4.9.2
libpcap version 1.5.3
OpenSSL 1.0.2k-fips 26 Jan 2017
Usage: tcpdump [-aAbdDefhHIJKlLnNOpqStuUvxX#] [ -B size ] [ -c count ][ -C file_size ] [ -E algo:secret ] [ -F file ] [ -G seconds ][ -i interface ] [ -j tstamptype ] [ -M secret ] [ --number ][ -Q|-P in|out|inout ][ -r file ] [ -s snaplen ] [ --time-stamp-precision precision ][ --immediate-mode ] [ -T type ] [ --version ] [ -V file ][ -w file ] [ -W filecount ] [ -y datalinktype ] [ -z postrotate-command ][ -Z user ] [ expression ]
i 指定网卡, tcp -i any 监听所有网卡
[root@aaa ~]# tcpdump -i eth0
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
14:03:56.016306 IP bogon.ssh > bogon.54416: Flags [P.], seq 1726969456:1726969652, ack 2933971251, win 264, length 196
14:03:56.016708 IP bogon.49387 > bogon.domain: 10222+ PTR? 1.0.0.10.in-addr.arpa. (39)
14:03:56.017502 IP bogon.54416 > bogon.ssh: Flags [.], ack 196, win 4106, length 0
14:03:56.020176 IP bogon.domain > bogon.49387: 10222* 1/0/0 PTR bogon. (58)
w
- 将捕获到的信息保存到文件中,且不分析和打印再屏幕。保留格式为pcap或cap可通过wireshark工具查看。
[root@aaa ~]# tcpdump -w file.pcap
tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
^C4 packets captured
6 packets received by filter
0 packets dropped by kernel
r
- 从文件(.cap或者.pcap的文件,直接cat不可见)中读取数据
[root@aaa ~]# tcpdump -r file.pcap
reading from file file.pcap, link-type EN10MB (Ethernet)
14:06:02.276568 IP bogon.ssh > bogon.54416: Flags [P.], seq 1726990416:1726990548, ack 2933974495, win 264, length 132
14:06:02.323979 IP bogon.54416 > bogon.ssh: Flags [.], ack 132, win 4100, length 0
14:06:02.882223 IP bogon.52254 > 239.255.255.250.ssdp: UDP, length 128
14:06:02.882250 IP bogon.52254 > 239.255.255.250.ssdp: UDP, length 129
n
- 不把ip转换为域名 ,直接显示ip,避免执行DNS lookup的过程,速度加快很多
[root@aaa ~]# tcpdump -n -i eth1
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth1, link-type EN10MB (Ethernet), capture size 262144 bytes
14:15:41.585776 IP 10.0.0.128.ssh > 10.0.0.1.54416: Flags [P.], seq 1728632928:1728633124, ack 2933982811, win 264, length 196
14:15:41.586362 IP 10.0.0.128.ssh > 10.0.0.1.54416: Flags [P.], seq 196:376, ack 1, win 264, length 180
14:15:41.586688 IP 10.0.0.128.ssh > 10.0.0.1.54416: Flags [P.], seq 376:524, ack 1, win 264, length 148
14:15:41.586882 IP 10.0.0.128.ssh > 10.0.0.1.54416: Flags [P.], seq 524:672, ack 1, win 264, length 148
nn
- 不把协议和端口号转换为名字。
[root@aaa ~]# tcpdump -nn -i eth1
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth1, link-type EN10MB (Ethernet), capture size 262144 bytes
14:17:16.647586 IP 10.0.0.128.22 > 10.0.0.1.54416: Flags [P.], seq 1728671064:1728671260, ack 2933983559, win 264, length 196
14:17:16.647955 IP 10.0.0.128.22 > 10.0.0.1.54416: Flags [P.], seq 196:376, ack 1, win 264, length 180
14:17:16.648121 IP 10.0.0.128.22 > 10.0.0.1.54416: Flags [P.], seq 376:524, ack 1, win 264, length 148
N 不打印出host的域名部分,比如域名www.baidu.com,只显示www. 10.0.0.128,只显示10
[root@aaa ~]# tcpdump -N -i eth1
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth1, link-type EN10MB (Ethernet), capture size 262144 bytes
14:18:29.782063 IP bogon.ssh > bogon.54416: Flags [P.], seq 1728776868:1728777064, ack 2933984531, win 264, length 196
14:18:29.782771 IP bogon.54416 > bogon.ssh: Flags [.], ack 196, win 4101, length 0
14:18:29.783472 IP bogon.39449 > bogon.domain: 21040+ PTR? 1.0.0.10.in-addr.arpa. (39)
t 不输出时间
[root@aaa ~]# tcpdump -t -i eth1
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth1, link-type EN10MB (Ethernet), capture size 262144 bytes
IP bogon.ssh > bogon.54416: Flags [P.], seq 1728970768:1728970964, ack 2933987275, win 264, length 196
IP bogon.33402 > bogon.domain: 51586+ PTR? 1.0.0.10.in-addr.arpa. (39)
IP bogon.54416 > bogon.ssh: Flags [.], ack 196, win 4103, length 0
tt 输出时间戳
[root@aaa ~]# tcpdump -tt -i eth1
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth1, link-type EN10MB (Ethernet), capture size 262144 bytes
1660803837.483092 IP bogon.ssh > bogon.54416: Flags [P.], seq 1729196976:1729197172, ack 2933988143, win 264, length 196
1660803837.483761 IP bogon.38173 > bogon.domain: 53503+ PTR? 1.0.0.10.in-addr.arpa. (39)
1660803837.484346 IP bogon.54416 > bogon.ssh: Flags [.], ack 196, win 4106, length
ttt 输出每两行打印的时间间隔
[root@aaa ~]# tcpdump -ttt -i eth1
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth1, link-type EN10MB (Ethernet), capture size 262144 bytes00:00:00.000000 IP bogon.ssh > bogon.54416: Flags [P.], seq 1729318904:1729319100, ack 2933988855, win 264, length 19600:00:00.001015 IP bogon.50985 > bogon.domain: 24775+ PTR? 1.0.0.10.in-addr.arpa. (39)00:00:00.000719 IP bogon.54416 > bogon.ssh: Flags [.], ack 196, win 4103, length 000:00:00.003056 IP bogon.domain > bogon.50985: 24775* 1/0/0 PTR bogon. (58)00:00:00.000231 IP bogon.47965 > bogon.domain: 9438+ PTR? 128.0.0.10.in-addr.arpa. (41)00:00:00.003084 IP bogon.domain > bogon.47965: 9438* 1/0/0 PTR bogon. (60)00:00:00.001147 IP bogon.39814 > bogon.domain: 15336+ PTR? 3.100.168.192.in-addr.arpa. (44)00:00:00.000968 IP bogon.ssh > bogon.54416: Flags [P.], seq 196:360, ack 1, win 264, length 16400:00:00.006849 IP bogon.domain > bogon.39814: 15336* 1/0/0 PTR bogon. (63)00:00:00.000449 IP bogon.ssh > bogon.54416: Flags [P.], seq 360:1100, ack 1, win 264, length 74000:00:00.000181 IP bogon.54416 > bogon.ssh: Flags [.], ack 1100, win 4106, length 0
tttt
- 在每行打印的时间戳之前添加日期的打印
[root@aaa ~]# tcpdump -tttt -i eth1
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth1, link-type EN10MB (Ethernet), capture size 262144 bytes
2022-08-18 14:25:50.104669 IP bogon.ssh > bogon.54416: Flags [P.], seq 1729405944:1729406140, ack 2933989619, win 264, length 196
2022-08-18 14:25:50.105199 IP bogon.48481 > bogon.domain: 44849+ PTR? 1.0.0.10.in-addr.arpa. (39)
2022-08-18 14:25:50.105452 IP bogon.54416 > bogon.ssh: Flags [.], ack 196, win 4103, length 0
2022-08-18 14:25:50.109160 IP bogon.domain > bogon.48481: 44849* 1/0/0 PTR bogon. (58)
v
- 产生详细的输出,如包的TTL,id标识,数据包长度以及IP包的一些选项,同时还会打开附加的包的完整性检测,比如对ip和icmp包头部的校验和。
[root@aaa ~]# tcpdump -v
tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
14:27:37.424336 IP (tos 0x10, ttl 64, id 24092, offset 0, flags [DF], proto TCP (6), length 172)bogon.ssh > bogon.54416: Flags [P.], cksum 0x151f (incorrect -> 0x2263), seq 1729695648:1729695780, ack 2933991875, win 264, length 132
14:27:37.425223 IP (tos 0x0, ttl 64, id 12318, offset 0, flags [DF], proto TCP (6), length 40)bogon.54416 > bogon.ssh: Flags [.], cksum 0x66c4 (correct), ack 132, win 4103, length 0
14:27:37.426048 IP (tos 0x0, ttl 64, id 53600, offset 0, flags [DF], proto UDP (17), length 67)bogon.43196 > bogon.domain: 53138+ PTR? 1.0.0.10.in-addr.arpa. (39)
vv 更详细
- 比如NFS的回应包中的附加域会被打印,SMB数据包也会被完全解码
vvv
- 产生更详细的输出,如telnet时所使用的SB.SE选项会被打印,如果telnet同时使用的是图形界面,其相应的图形界面将会以16进制的方式打印出来。
c
- 指定收取数据包的次数,在收到指定数据包的数量后,抓包结束
[root@aaa ~]# tcpdump -c 10
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
14:32:41.401248 IP bogon.ssh > bogon.54416: Flags [P.], seq 1729745680:1729745876, ack 2933992991, win 264, length 196
14:32:41.402237 IP bogon.50414 > bogon.domain: 11574+ PTR? 1.0.0.10.in-addr.arpa. (39)
14:32:41.402859 IP bogon.54416 > bogon.ssh: Flags [.], ack 196, win 4103, length 0
14:32:41.406165 IP bogon.domain > bogon.50414: 11574* 1/0/0 PTR bogon. (58)
14:32:41.406747 IP bogon.50236 > bogon.domain: 52277+ PTR? 128.0.0.10.in-addr.arpa. (41)
14:32:41.410414 IP bogon.domain > bogon.50236: 52277* 1/0/0 PTR bogon. (60)
14:32:41.410706 IP bogon.50301 > bogon.domain: 65461+ PTR? 3.100.168.192.in-addr.arpa. (44)
14:32:41.410856 IP bogon.ssh > bogon.54416: Flags [P.], seq 196:360, ack 1, win 264, length 164
14:32:41.414218 IP bogon.domain > bogon.50301: 65461* 1/0/0 PTR bogon. (63)
14:32:41.414570 IP bogon.ssh > bogon.54416: Flags [P.], seq 360:1084, ack 1, win 264, length 724
10 packets captured
10 packets received by filter
0 packets dropped by kernel
参数C
- 与-w FILE 选项配合使用该选项,使得tcpdump在把原始数据包直接保存到文件中之前,检查此文件大小是否超过file-size。如果超过了,将关闭此文件,另创一个文件继续保存原始数据包。新创建的文件名与-w选项指定的文件名一致,但文件名后多了一个数字,该数字会从1开始随着新创建文件的增多而增加。
tcpdump -C 1 -W 3-w abc #fle-size的单位是百万字节(这里指1,000,000个字节,并非1,048,576个字节)指定一个单位后(1MB)就换文件,最多写3个文件,名字是abco,abc1,abc2。
Q
- 选择是入方向还是出方向的数据包,可选项有:in,out ,inout,也可使用–direction=[direction]
[root@aaa ~]# tcpdump -c 5 -Q in
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
14:52:32.364424 IP bogon.54416 > bogon.ssh: Flags [.], ack 1729776340, win 4105, length 0
14:52:32.368218 IP bogon.domain > bogon.47612: 55047* 1/0/0 PTR bogon. (60)
14:52:32.371664 IP bogon.domain > bogon.49149: 21414* 1/0/0 PTR bogon. (58)
14:52:32.377399 IP bogon.domain > bogon.47866: 60118* 1/0/0 PTR bogon. (63)
14:52:32.377866 IP bogon.54416 > bogon.ssh: Flags [.], ack 409, win 4103, length 0
5 packets captured
11 packets received by filter
0 packets dropped by kernel
[root@aaa ~]# tcpdump -c 5 --direction in
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
14:52:59.578433 IP bogon.54416 > bogon.ssh: Flags [.], ack 1729777968, win 4104, length 0
14:52:59.582852 IP bogon.domain > bogon.43124: 22463* 1/0/0 PTR bogon. (60)
14:52:59.586559 IP bogon.domain > bogon.42541: 1981* 1/0/0 PTR bogon. (58)
14:52:59.591720 IP bogon.domain > bogon.53639: 64160* 1/0/0 PTR bogon. (63)
14:52:59.592559 IP bogon.54416 > bogon.ssh: Flags [.], ack 409, win 4102, length 0
5 packets captured
11 packets received by filter
0 packets dropped by kernel
q
- 简洁的打印,打印很少的协议相关信息。
[root@aaa ~]# tcpdump -c 5 -q
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
14:54:18.078853 IP bogon.ssh > bogon.54416: tcp 196
14:54:18.079462 IP bogon.53699 > bogon.domain: UDP, length 39
14:54:18.085794 IP bogon.domain > bogon.53699: UDP, length 58
14:54:18.086884 IP bogon.48566 > bogon.domain: UDP, length 41
14:54:18.092185 IP bogon.domain > bogon.48566: UDP, length 60
5 packets captured
9 packets received by filter
0 packets dropped by kernel
D 显示所有可用的网络接口列表。
[root@aaa ~]# tcpdump -D
1.eth0
2.bluetooth0 (Bluetooth adapter number 0)
3.nflog (Linux netfilter log (NFLOG) interface)
4.nfqueue (Linux netfilter queue (NFQUEUE) interface)
5.eth1
6.usbmon1 (USB bus number 1)
7.usbmon2 (USB bus number 2)
8.any (Pseudo-device that captures on all interfaces)
9.lo [Loopback
L 列出网络接口的已知数据链路
[root@aaa ~]# tcpdump -L
Data link types for eth0 (use option -y to set):EN10MB (Ethernet)DOCSIS (DOCSIS) (printing not supported)
s
- 指定每个包的捕获长度,单位是byte,而不是默认的262144bytes;如果超过了设定的大小限制,包就会被截断而在打印行出现【proto】这种标识,这个proto就是被截断的报文的协议名字。但是抓取len越长,包的处理时间越长,并且会减少tcpdump可缓存的数据包的数量,从而会导致数据包的丢失,所以在能抓取我们想要的包的前提下,抓取长度越小越好(-s0 使用默认长度262144),但不同版本的tcpdump默认抓取的报文长度不一样。
[root@aaa ~]# tcpdump tcp port 53
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes ## 修改此处262144
[root@aaa ~]# tcpdump -s 20 -c 5
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 20 bytes
15:01:21.311838 IP [|ip]
15:01:21.312102 IP [|ip]
15:01:21.312188 IP [|ip]
15:01:21.312256 IP [|ip]
15:01:21.312345 IP [|ip]
5 packets captured
5 packets received by filter
0 packets dropped by kernel
V 查看版本
[root@aaa ~]# tcpdump -V
tcpdump: option requires an argument -- 'V'
tcpdump version 4.9.2
libpcap version 1.5.3
OpenSSL 1.0.2k-fips 26 Jan 2017
Usage: tcpdump [-aAbdDefhHIJKlLnNOpqStuUvxX#] [ -B size ] [ -c count ][ -C file_size ] [ -E algo:secret ] [ -F file ] [ -G seconds ][ -i interface ] [ -j tstamptype ] [ -M secret ] [ --number ][ -Q|-P in|out|inout ][ -r file ] [ -s snaplen ] [ --time-stamp-precision precision ][ --immediate-mode ] [ -T type ] [ --version ] [ -V file ][ -w file ] [ -W filecount ] [ -y datalinktype ] [ -z postrotate-command ][ -Z user ] [ expression ]
A 以ASCII格式(真实内容)打印出所有的分组并且读取此文件
[root@aaa ~]# tcpdump -A -r file.pcap #读取已有文件
reading from file file.pcap, link-type EN10MB (Ethernet)
14:06:02.276568 IP bogon.ssh > bogon.54416: Flags [P.], seq 1726990416:1726990548, ack 2933974495, win 264, length 132
E... .@.@...
...
.......f..P....P.............5..Q.#<..sD....;$../..|9J.e0.....>.4....=.......-....e........#.y:HLoivn.Ik#...E:.g../.a....^6.....\...%..T...0.*.p..!...(;F=.
14:06:02.323979 IP bogon.54416 > bogon.ssh: Flags [.], ack 132, win 4100, length 0
E..(..@.@..a
...
...........f...P....$........
14:06:02.882223 IP bogon.52254 > 239.255.255.250.ssdp: UDP, length 128
E...K.....uo
..........l..q.M-SEARCH * HTTP/1.1
Host:239.255.255.250:1900
ST:urn:schemas-upnp-org:service:WANIPConnection:1
Man:"ssdp:discover"
MX:314:06:02.882250 IP bogon.52254 > 239.255.255.250.ssdp: UDP, length 129
E...K.....um
..........l..[.M-SEARCH * HTTP/1.1
Host:239.255.255.250:1900
ST:urn:schemas-upnp-org:service:WANPPPConnection:1
Man:"ssdp:discover"
MX:3
配合grep使用
[root@aaa ~]# tcpdump -A | grep baidu.com
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
15:08:30.190025 IP bogon.34439 > bogon.domain: 24886+ A? baidu.com. (27)
.....d....5.#/`a6...........baidu.com.....
15:08:30.190147 IP bogon.34439 > bogon.domain: 16200+ AAAA? baidu.com. (27)
.....d....5.#/`?H...........baidu.com.....
....5...N..?H...........baidu.com..................dns...sa..w......,...,.'.....
....5...C..a6...........baidu.com.................n.DB............'.BX 表示同时使用十六进制和ASCII字符串打印报文的全部数据, X 和 A两个参数不能同时使用
[root@aaa ~]# tcpdump -X -c 1
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
15:12:43.200589 IP bogon.ssh > bogon.54416: Flags [P.], seq 1732250880:1732251076, ack 2934021887, win 264, length 1960x0000: 4510 00ec 7908 4000 4006 ac73 0a00 0080 E...y.@.@..s....0x0010: 0a00 0001 0016 d490 6740 0d00 aee1 9eff ........g@......0x0020: 5018 0108 155f 0000 43b6 939e 0114 3262 P...._..C.....2b0x0030: dd11 ff72 6ce8 526d b46b ce08 414c d92a ...rl.Rm.k..AL.*0x0040: 7054 5b66 cb1e 5227 baad deb3 bac0 47a7 pT[f..R'......G.0x0050: e809 a2d4 28ab 9fd2 5cb6 96bf 3642 ce3a ....(...\...6B.:0x0060: 3fe7 81a5 13f9 fdd5 2ff4 07db 3f97 d0dc ?......./...?...0x0070: 2914 1f51 4d91 936e 28fa 61c8 cdae 34fa )..QM..n(.a...4.0x0080: fc05 5926 cef1 b044 75c6 f603 33e0 7e42 ..Y&...Du...3.~B0x0090: 29b8 e2fb 825e a587 43d4 23b7 aff2 be7b )....^..C.#....{0x00a0: a53e ffd2 4fdc c8e0 bf52 47b3 d4c7 434e .>..O....RG...CN0x00b0: d6a2 e264 900f cc09 45be 5448 2bc3 1ca6 ...d....E.TH+...0x00c0: 8522 d0f7 805a 6917 e105 8bba bf49 71b3 ."...Zi......Iq.0x00d0: 7ea0 24e5 1ae8 8233 1337 a2f9 6b9b a5df ~.$....3.7..k...0x00e0: 18b0 5974 51b2 1564 0082 faf8 ..YtQ..d....
1 packet captured
5 packets received by filter
0 packets dropped by kernel
[root@aaa ~]# tcpdump -X | grep 128
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
15:23:12.534166 IP bogon.41897 > bogon.domain: 64188+ PTR? 128.0.0.10.in-addr.arpa. (41)0x0020: 0001 0000 0000 0000 0331 3238 0130 0130 .........128.0.00x0020: 0001 0001 0000 0000 0331 3238 0130 0130 .........128.0.0
^[[A 0x0040: 8859 f1da e8a4 f285 7dbb c722 187c 9128 .Y......}..".|.(
e
- 在输出行打印出数据链路层的头部信息,默认情况下tcpdump不会显示该信息,可用-e参数后可显示源和目的mac地址,以及VLAN tag信息等。
[root@aaa ~]# tcpdump -e -c 2
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
15:24:04.004298 00:0c:29:1f:1b:19 (oui Unknown) > 00:50:56:c0:00:08 (oui Unknown), ethertype IPv4 (0x0800), length 250: bogon.ssh > bogon.54416: Flags [P.], seq 1733009276:1733009472, ack 2934032319, win 264, length 196
15:24:04.004872 00:0c:29:1f:1b:19 (oui Unknown) > 00:50:56:e9:82:79 (oui Unknown), ethertype IPv4 (0x0800), length 81: bogon.41923 > bogon.domain: 45738+ PTR? 1.0.0.10.in-addr.arpa. (39)
2 packets captured
9 packets received by filter
0 packets dropped by kernel
-F
- 指定使用哪个文件的过滤表达式抓包。此时命令行上的输入过滤规则将被忽略。这种情况适用于将表达式放置在文件中长期维护。
root@aaa ~]# cat filter_file
tcp port 80
[root@aaa ~]# tcpdump -F filter_file
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
-l
- 对标准输出进行 行缓冲,使标准输出设备遇到一个换行符就马上把这行内容打印出来。在需要同时观察抓包打印以及保存抓包记录的时候很有用.
比如,可通过以下命令组合来达到此抓包时并保存到文件的同时查看包的内容。
[root@aaa ~]# tcpdump -l | tee aa # aa是文件名称
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
15:32:55.041400 IP bogon.ssh > bogon.54416: Flags [P.], seq 1733027644:1733027840, ack 2934039975, win 264, length 196
15:32:55.094617 IP bogon.54416 > bogon.ssh: Flags [.], ack 196, win 4103, length 0
15:32:55.482779 IP bogon > 110.242.68.66: ICMP echo request, id 3185, seq 246, length 64
15:32:55.497044 IP 110.242.68.66 > bogon: ICMP echo reply, id 3185, seq 246, length 64
15:32:55.497245 IP bogon.ssh > bogon.62816: Flags [P.], seq 232445022:232445154, ack 2655284463, win 264, length 132
15:32:55.545036 IP bogon.62816 > bogon.ssh: Flags [.], ack 132, win 4106, length 0
15:32:55.671823 IP bogon.59270 > 239.255.255.250.ssdp: UDP, length 175
^C7 packets captured
27 packets received by filter
0 packets dropped by kernel
- 这命令是使用tee来把tcpdump的输出同时放到文件aa和标准输出中。
- tee功能说明:读取标准输入的数据,并将其内容输出成文件这个命令是通过重定向操作 重定向操作,效果同上
[root@aaa ~]# tcpdump -l > aa & tail -f aa
TCPDUMP过滤规则组合–逻辑运算
逻辑运算符:and or not
and:所有的条件都需要满足,也可以表示为 &&
or:只要有一个条件满足就可以,也可以表示为 ||
not:取反,也可以使用!
and例子
[root@aaa ~]# tcpdump src 10.0.61.61 and port 22
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
or例子
[root@aaa ~]# tcpdump tcp port 53 or udp port 53
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
not例子
root@aaa ~]# tcpdump not tcp port 22
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
15:56:55.731411 IP bogon.62255 > 239.255.255.250.ssdp: UDP, length 175
15:56:55.732192 IP bogon.56817 > bogon.domain: 31651+ PTR? 250.255.255.239.in-addr.arpa. (46)
15:56:55.738337 IP bogon.domain > bogon.56817: 31651 NXDomain 0/1/0 (103)
15:56:55.739861 IP bogon.37923 > bogon.domain: 12708+ PTR? 1.0.0.10.in-addr.arpa. (39)
15:56:55.743889 IP bogon.domain > bogon.37923: 12708* 1/0/0 PTR bogon. (58)
- 多个过滤器进行组合(and优先级高于or):需要用到括号,而括号在shell中是特殊符号,因为你需要使用引号将其包含:
[root@aaa ~]# tcpdump "src 10.0.61.61 and (dst port 22)"
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
- 监听主机10.0.61.61 和10.0.0.128之间ip协议的80端口的且排除www.baidu.com通信的所有数据包。
[root@aaa ~]# tcpdump ip dst 10.0.61.61 and src 10.0.0.128 and port 80 and host ! www.baidu.com #not和!都是相同的取反的意思
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
TCPDUMP高级过滤
基于 包大小进行过:查看指定大小的数据包 less greater
[root@aaa ~]# tcpdump less 100 -c 5 #小于100字节
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
16:21:00.871792 IP bogon.62816 > bogon.ssh: Flags [.], ack 232651638, win 4100, length 0
16:21:00.872534 IP bogon.39648 > bogon.domain: 51119+ PTR? 128.0.0.10.in-addr.arpa. (41)
16:21:00.875951 ARP, Request who-has bogon tell bogon, length 46
16:21:00.875965 ARP, Reply bogon is-at 00:0c:29:1f:1b:19 (oui Unknown), length 28
16:21:00.876270 IP bogon.39861 > bogon.domain: 21871+ PTR? 1.0.0.10.in-addr.arpa. (39)
5 packets captured
9 packets received by filter
0 packets dropped by kernel
补充 ALG穿透 SIP
SIP(Session initialization Protocol,会话初始协议)是由IETF(Internet Engineering Task Force,因特网工程任务组)制定的多媒体通信协议。
它是一个基于文本的应用层控制协议,用于创建、修改和释放一个或多个参与者的会话。SIP 是一种源于互联网的IP 语音会话控制协议,具有灵活、易于实现、便于扩展等特点。
详情描述
公司部署有IP电话业务,客户端发起语音电话请求业务云端服务器,云端服务器下发至公司客户端,IP电话能正常拨打接通,但在业务后台显示无此会话记录,导致IP电话业务异常,排查后发现:AD设备ALG穿透原理是将数据包应用层内容修改替换,例如私有IP替换为公网IP地址,主要用于语音、视频会议、FTP服务器等业务场景。关闭sip后依旧无法使用,排除AD设备问题。
这篇关于【TCPDUMP 笔记 2022.8.18】的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!







